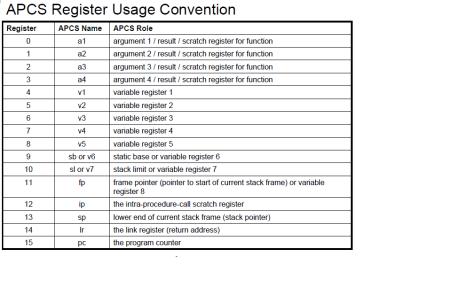
SDMA interrupt entry is added in init_intrinfo().
Identify SDMA interrupt source. * * Returns interrupt number in r4 * ----------------------------------------------------------------------- */ CALLOUT_START(interrupt_id_omap4_sdma, 0, interrupt_patch_sdma) /* * Get the interrupt controller base address (patched) */ mov ip, #0x000000ff orr ip, ip, #0x0000ff00 orr ip, ip, #0x00ff0000 orr ip, ip, #0xff000000 /* * Read Interrupt Mask and Status */ ldr r3, [ip, #SDMA_IRQSTATUS] // Status ldr r2, [ip, #SDMA_IRQENABLE] // Mask and r3, r3, r2 /* * Scan for first set bit */ #if 0 mov r4, #32 mov r1, #1 0: subs r4, r4, #1 blt 1f tst r3, r1, lsl r4 beq 0b #else clz r4, r3 rsbs r4, r4, #31 blt 1f mov r1, #1 #endif /* * Mask the interrupt source */ mov r1, r1, lsl r4 bic r2, r2, r1 str r2, [ip, #SDMA_IRQENABLE] ldr r2, [ip, #SDMA_IRQENABLE] /* * Clear interrupt status * 09.17.2014: clearing the staus bit is moved to the eoi-callout since the status bit related * to a channel can only be claered if the channel status register of the associated * channel is cleared. Clearing the csr can't be done in a generic way here because the attached * isterrupt service routines need to know the interrupt reason (block, fram, drop etc. ...) */ //str r1, [ip, #SDMA_IRQSTATUS] 1: CALLOUT_END(interrupt_id_omap4_sdma) /* * ----------------------------------------------------------------------- * Acknowledge specified SDMA interrupt * * On entry: * r4 contains the interrupt number * r7 contains the interrupt mask count * ----------------------------------------------------------------------- */ CALLOUT_START(interrupt_eoi_omap4_sdma, 0, interrupt_patch_sdma) /* * Get the interrupt controller base address (patched) */ mov ip, #0x000000ff orr ip, ip, #0x0000ff00 orr ip, ip, #0x00ff0000 orr ip, ip, #0xff000000 /* * Only unmask interrupt if mask count is zero */ teq r7, #0 bne 0f /* * Clear interrupt status * see comment in the id-callout */ mov r2, #1 mov r2, r2, lsl r4 str r2, [ip, #SDMA_IRQSTATUS] ldr r1, [ip, #SDMA_IRQENABLE] orr r1, r1, r2 str r1, [ip, #SDMA_IRQENABLE] 0: CALLOUT_END(interrupt_eoi_omap4_sdma)